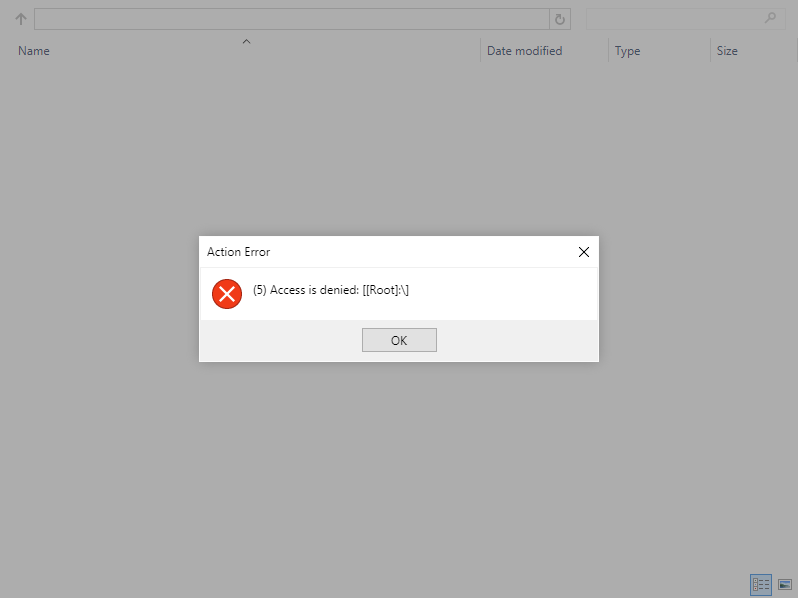
I have a MVC web application that works great with the File Ultimate plugin. I followed the guide on your main site and everything works wonderful. I deployed my code to our web server and I get an error that states: "(5) Access is denied".
After doing some digging, this is due to the web servers IIS attempting to access a UNC path that it does not have permission to, thus failing. I tried updating my applications web.config to the below using my personal username/password and it worked.
<location path="filemanager.ashx">
<system.web>
<identity impersonate="true" userName="JohnDoe" password="password123" />
</system.web>
</location>Unfortunately, I don't want to use my personal username/password OR any hardcoded username/password for this website. I want the windows authenticated user who is logged in the website to use their account to access the UNC path. I tried removing username/password hoping it would grab the users login information, but it did not. You still get the "(5) Access is denied" with the below entry in your web.config.
How do I successfully get a user to access a UNC path via a web server and not get "(5) Access is denied"?
<location path="filemanager.ashx">
<system.web>
<identity impersonate="true" />
</system.web>
</location>
*UPDATE*
I saw another
post about setting User Authentication = True in the code.
Location = "Path=SOMEPATH; Authenticated User=true"
I tried the following, but still no luck. Any thoughts on what I could be doing wrong?
var fileManager = new FileManager
{
Width = 800,
Height = 600,
Resizable = true,
ShowFoldersPane = false,
ShowRibbon = false,
ViewLayout = ViewLayout.Details
};
var rootFolder = new FileManagerRootFolder
{
Name = "Root",
Location = "Path=\\abcs8080bbb01-cifs\directory\folder; Authenticated User=true"
};
rootFolder.AccessControls.Add(new FileManagerAccessControl
{
Path = @"\",
AllowedPermissions = FileManagerPermissions.Full
});
fileManager.RootFolders.Add(rootFolder);
<head>
<title>File Manager</title>
@this.RenderHead(fileManager)
</head>
<body>
@this.RenderBody(fileManager)
</body>*Update 2*
rootFolder.Location = @"Path=\\server\share; Authenticated User=Windows";
Found exactly what I was looking for, but I still cannot get the shared drive to display the files! I updated my code block to what I'm trying. What am I doing wrong?
var fileManager = new FileManager
{
Width = 800,
Height = 600,
Resizable = true,
ShowFoldersPane = false,
ShowRibbon = false,
ViewLayout = ViewLayout.Details
};
var rootFolder = new FileManagerRootFolder();
rootFolder.Name = "Root";
rootFolder.Location = @"Path=\\njtclda01-server\directory\example; Authenticated User=Windows";
rootFolder.AccessControls.Add(new FileManagerAccessControl
{
Path = @"\",
AllowedPermissions = FileManagerPermissions.Full
});
fileManager.RootFolders.Add(rootFolder);
<head>
<title>File Manager</title>
@this.RenderHead(fileManager)
</head>
<body>
@this.RenderBody(fileManager)
</body>